33.2 Client Information tab
Complete the following sections on this tab:
33.2.1 Client Information
|
Field |
Description |
|---|---|
|
Client name |
Your company’s name. The name provided here will be displayed on the Apata portal as the Financial institution name. |
|
Country of residence |
Your company’s country of residence. |
|
Scheme |
Card scheme (e.g., Visa or Mastercard). |
|
Issuer name |
The name of your issuer (BIN sponsor). |
|
Visa BID |
Your issuer’s (BIN sponsor) Visa Business Identifier (BID) |
|
Mastercard Primary ICA Number |
Your issuer’s (BIN sponsor) primary ICA |
|
Mastercard Company Name (Issuer) |
Your issuer’s (BIN sponsor) Company Name, as registered with Mastercard. |
|
Mastercard Company ID (CID) |
Your issuer’s (BIN sponsor) Company ID, as registered with Mastercard. |
|
Thredd Program Manager ID |
Your Thredd Program ID or code. Assigned by Thredd. |
|
UAT readiness date |
Date when you plan to be ready to test 3D Secure in the UAT environment. |
|
Planned Go Live date |
Date when you plan to launch 3D Secure for your card programme. Please check with your Implementation Manager to confirm that this date is feasible. For steps and indicative time scales to launch a 3D Secure service, see Steps in a 3D Secure Biometric/In-app Project. |
|
Do you require Thredd to validate the AAV/CAVV? |
The AAV/CAVV If YES: Thredd will validate the AAV/CAVV
If NO:
|
|
Type of webservice to be used for 3DS enrolment |
API to use for card enrolment. Options include:
For more information, see Using the Card Enrolment API. |
|
Thredd Environment under which Program Manager is set up |
Environment options include:
|
For more details, refer to the instructions in the 3DS Product Setup Form (PSF).
33.2.2 Required authentication methods
|
|
|
|---|---|
|
OOB other |
The cardholder receives an issuer-generated push notification to authenticate within the authenticator or mobile banking app. |
|
OOB Biometrics |
The cardholder receives an issuer-generated push notification to authenticate within the authenticator or mobile banking app using a biometric identifier; for example face ID or fingerprint. |
|
OTP via Email |
The cardholder receives a One-Time Passcode (OTP) via email. |
|
OTP via SMS |
The cardholder receives a One-Time Passcode (OTP) via SMS (text message). |
|
KBA - Transaction history |
Knowledge Based Authentication (KBA). The cardholder is presented with a Challenge screen asking them to identify a recent payment they made on the card. |
|
KBA - custom question |
Knowledge Based Authentication (KBA). The cardholder is presented with a Challenge screen asking them to provide the answer to a question they have previously supplied. |
|
OTP via SMS + KBA |
The cardholder is first requested to authenticate using OTP via SMS and then by KBA. |
|
OTP via Email + KBA |
The cardholder is first requested to authenticate using OTP via email and then by KBA. |
33.2.3 Setup options
|
Field |
Description |
|---|---|
|
Default language |
Default language to apply to all cardholder Challenge screens, configured at product level. |
|
Other languages |
List any additional languages you support. You will also need to specify which language to apply to each card product. Otherwise, the default language will be applied to all products. See Challenge Screens > Supported Languages. |
|
Default authentication |
Select the default authentication type to support all BINs or sub-BIN ranges. See the drop down on the 3D Secure PSF for all available options. This is used for the following purposes: a) to enable a card to be enrolled in this type; b) to use as the default type of authentication during a real-time authentication session with Apata; c) to support auto-enrolment. |
|
Fallback authentication |
Select the fallback authentication type to support all sub-BIN ranges.See the drop down on the 3D Secure PSF for all available options. This is used for two purposes: a) to enable a card to be enrolled in this type; b) to use as the fallback type of authentication during a real-time authentication session with Apata, if the default type cannot be used for any reason. |
|
Enable SMS OTP auto enrolment |
Options are: NO — All cards must be enrolled for OTP SMS and the mobile number must be registered using either the Thredd API or the Cards API; see Using the Card Enrolment API. YES - Initial Load — Thredd enrol the existing cards to the OTP SMS credential. Thredd use the phone number linked to the card (i.e., the phone number supplied when the card was created or updated). YES - Continuous — Same as Initial load, however any future cards created will also have their phone numbers automatically registered for 3D Secure in the same way. If using Continuous auto-enrolment, this may restrict your ability to unenroll cards that have been previously enrolled and which currently have a live status. For details, please speak to your 3DS Project Manager. |
|
Enable Biometric auto enrolment |
Options are:
|
|
Enable Email OTP auto enrolment |
Options are:
|
|
Time to complete authentication in seconds. Countdown timer will be displayed in the Challenge screen. This is customisable up to 10 minutes (600 seconds) as per EMVCo requirements. The standard is 300 seconds (5 minutes). If a fallback method is initiated, the timer will be restarted for the new authentication method. |
|
|
DelegateSCANotification endpoint - UAT |
For Out of Band and Biometric authentication, and to access the Thredd oAuth endpoint, in the UAT environment. Your endpoint for receiving the Please only supply one endpoint for the UAT environment. Please ensure that the provided endpoint is resolving to one or set of (maximum 5) Static IP addresses. |
|
DelegateSCAValidation IP Address - UAT |
For Out of Band and Biometric authentication, and to access the Thredd oAuth endpoint, in the UAT environment. Please provide your endpoint IP addresses for connection to the UAT environment. This should be no more than 5 static IP addresses. |
|
DelegateSCANotification endpoint - Production |
For Out of Band and Biometric authentication only in the Production environment. Your endpoint for receiving the Please only supply one endpoint for the UAT environment, and one endpoint for the Production environment. Please ensure that the provided endpoint is resolving to one or set of (maximum 5) Static IP addresses. |
|
DelegateSCAValidation IP Address - Production |
For Out of Band and Biometric authentication only in the Production environment. Please provide your endpoint IP addresses for connection to the Production environment. This should be no more than 5 static IP addresses. |
|
KBA number of questions to answer |
Total number of questions which the cardholder is required to answer. |
|
KBA number of correct answers required |
Total number of questions which the cardholder is required to answer correctly to successfully authenticate the transaction. |
|
KBA number of incorrect answers permitted |
Total number of questions that the cardholder may answer incorrectly before KBA is failed. |
|
Number of retries allowed for OTP (Email/SMS) |
The number of times that a cardholder can request for a new OTP to be resent via SMS or Email. The standard retry is 3, however this can be increased up to 5 retries. |
|
Number of attempts allowed for OTP (Email/SMS) |
The number of times that a cardholder can input the wrong value and still continue the process. After this the authorisation will decline and would need to be re-attempted. |
|
Number of attempts allowed for KBA authentication |
The number of times that a cardholder can enter the incorrect answer for each question. We recommend you keep this at a minimum to prevent brute force attack. |
|
SMS Sender ID |
Text that appears as the sender of the SMS OTP (e.g., Program Manager name or Card brand). Can be up to 11 alphanumeric characters with no spaces. This Sender ID will be used for all SMS services. Please make sure to match this with |
|
Email OTP sender |
The "From" email address for the email OTP (i.e., from your organisation). Apata will complete the registration to send the OTP Email to your cardholders on your organisation's behalf. An authorisation email will be initiated to the email domain administrator. Authorisation will be required via the link in the email to complete the setup. |
|
Dashboard currency |
Currency to be applied to the dashboard in Apata. This will apply across your card programme. |
33.2.4 OTP SMS Text Support
For OTP SMS messages (sent by Thredd to the cardholder’s phone number), the SMS message is dynamic, and you can specify the text and variables to use. See Appendix 2: OTP Message Templates.
Please contact your Thredd 3DS project manager to ask for these SMS options to be configured.
Language is determined by checking the current value of the card’s language setting (if using Thredd API![]() The Thredd API consists of web services that use SOAP and the Cards API based on REST., see the Web Services Guide >Create Card; if using our Cards API
The Thredd API consists of web services that use SOAP and the Cards API based on REST., see the Web Services Guide >Create Card; if using our Cards API![]() The Thredd Cards API are REST-based API that enable you to create and manage the cards in your card programme using JSON messages., see the Cards API Website > Creating a Card). Below is an example of the OTP SMS message, in French:
The Thredd Cards API are REST-based API that enable you to create and manage the cards in your card programme using JSON messages., see the Cards API Website > Creating a Card). Below is an example of the OTP SMS message, in French:
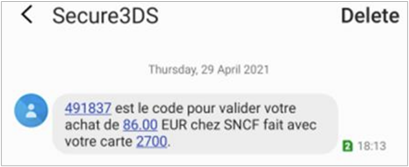
Figure 51: OTP SMS Message Example
A single SMS message can contain up to 140 bytes of information. The number of characters which can be included in a single SMS message depends on the type of characters the message contains. Depending on the recipient's mobile carrier and device, multiple messages may be displayed as a single message, or as a sequence of separate messages. If you are looking to avoid OTP message split into multiple parts then our recommendation is to keep it brief.
Thredd uses the default English text below if no customised message is configured (provided that the merchant shares all transactional information).
"{{OTP}} is the One Time Passcode required for completing a purchase of {{CUR}} {{Amount}} at {{MerchantName}} with the last four digits of your card ending in {{CardNumber}}." Please use the One Time Passcode to complete the transaction.