In-App Push Provisioning
In-App Push Provisioning enables a cardholder to request a token for their device directly from the Programme Manager's mobile app, removing the need to manually enter the PAN details into the mobile wallet Token Requestor's app.
Since it originates from inside the mobile app, the Program Manager can pre-authenticate the cardholder through entry to their mobile app before a request for a token is sent to the Token Service Provider (such as Visa or Mastercard). For information on the requirements for authenticating a cardholder during push provisioning, discuss with your mobile wallet Token Requestor.
In-App Push provisioning requires you to share sensitive card data with the Token Service Provider using the mobile wallet Token Requestor. This data needs to be encrypted to standards of both the Token Service Provider and the mobile wallet Token Requestor. Thredd's role is to provide an encrypted payload that can be returned to your mobile app and passed into the relevant mobile wallet app.
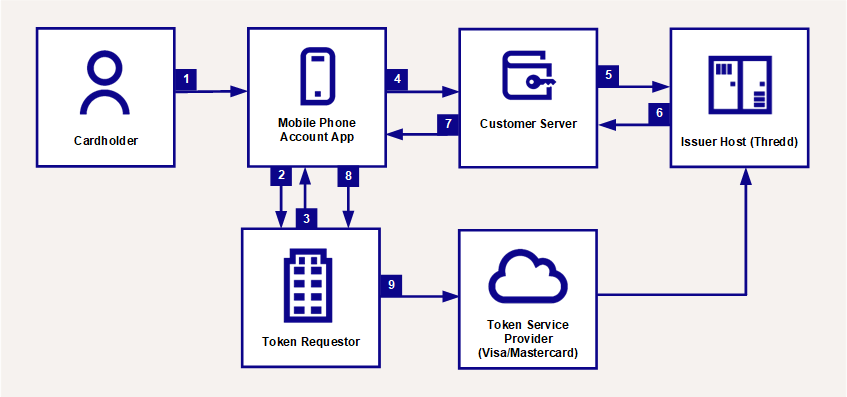
Figure: In-App Push Provisioning
-
The cardholder confirms the card to be added to their mobile phone application for your service.
-
Your mobile phone app requests encrypted card data for In-App Provisioning from the token requestor (e.g., Apple or Android).
-
The token requestor returns the data.
-
Your mobile app sends data to your server.
-
Using a valid REST API authorisation token, your server calls either the Thredd Apple or Google Wallet endpoint.
-
Thredd creates an encrypted payload and returns it to your server.
-
The server sends the encrypted data to the mobile phone app.
-
The encrypted data is passed to the token requestor from the phone app.
-
The token requestor initiates provisioning with the Token Service Provider, which decrypts the card data and starts the token provisioning flow.
For more information on the Thredd Tokenisation Service, see the Tokenisation Service Guide.